This document describes how to use Gnu Privacy Assistant (GPA) to set up the Crypto Stick for its first usage.

This is a guide to using YubiKey as a SmartCard for storing GPG encryption, signing and authentication keys, which can also be used for SSH. Many of the prin. ★ TRUSTED SECURITY: GnuPG already seamlessly integrates into Mac OSX (GPGtools), Windows (gpg4win), GNU/Linux, Debian, Ubuntu, Fedora. ★ OPEN STANDARD COMPLIANT: Full OpenPGP implementation following RFC2440 and RFC4880.
Gnu Privacy Assistant Clipboard
If you need multiple people to be able to decrypt high security exports and are using GPA to manage keys and encryption/decryption in a Windows desktop environment, please follow these simple steps. GnuPG is a hybrid-encryption software program because it uses a combination of conventional symmetric-key cryptography for speed, and public-key cryptography for ease of secure key exchange, typically by using the recipient's public key to encrypt a session key which is used only once. This mode of operation is part of the OpenPGP standard and has been part of PGP from its first version.
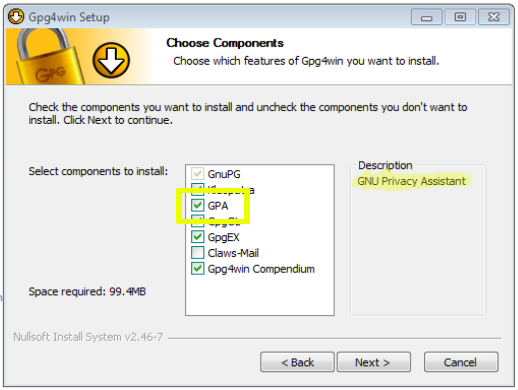
- First you need to install Gnu Privacy Assistant (GPA). For Windows you should download and install the GPG4Win package which contains GPA. For Linux you should install the GPA package of your distribution (e.g. on Ubuntu: sudo apt-get install gpa ).
- Start GPA and select the Card Manager; either by pressing the icon at the top or by choosing Card Manager in the Windows menu.
- The window of the Card Manager will appear. Enter your salutation, name and optional other information. While doing so you might be asked to enter the admin PIN.
- Confirm this window and enter the admin PIN in the next window.
- In the Card Manager window you might need to scroll down until you see the buttons to change the PINs. The term PIN is used interchangeable with 'password'. Press the first button 'Change PIN' in order to change the user password. Read and confirm the following information window.
- Choose and enter your own PIN with a minimum length of six characters. This PIN is required for the daily usage of the Crypto Stick.
- Go back to the Card Manager window in step three. This time you choose the third button Change PIN in order to change the admin PIN. The admin PIN is required to change the information on the Crypto Stick and to change the cryptographic keys. Proceed as described in steps four and five.
- After changing both the user and the admin PIN, you are back in the Card Manager window. Select 'Generate key' in the 'Card' menu.
- Enter your name and e-mail address. You should keep 'backup' enabled in order to create a backup file of your cryptographic keys. Optionally you might select an expiration date for your cryptographic keys.
- Wait until the keys are generated successfully.
- Enter a strong passphrase for your backup keys. We strongly recommend to store the backup file on a separate storage(e.g. CD-ROM) and on a safe location.
- Congratulations, your Crypto Stick is now ready to use. Please see the applications section for further information of its usage.
Gnu Privacy Guard Download
- Global Nav Open Menu Global Nav Close Menu; Apple; Shopping Bag +. Search Support.
- Feb 01, 2016.